-
Tags
-
Author
-
Evelina Sinkevičiūtė
-
December 24, 2019
Zero Trust architecture is a set of guiding principles that rely on the key assumption that the corporate network is a hostile environment. Thus, the company network infrastructure is not more secure than any other network and each access must be independently authorized and authenticated. Zero Trust architecture helps reduce uncertainty and improves control and visibility into secure access.
To ensure security, the enterprise must continuously analyze and assess risks to its internal resources, business apps, and workloads. Zero Trust architecture not only restricts access to resources to only those who must have it, but also goes beyond the concept of Role-based access control (RBAC) to implement Attribute-based access control (ABAC) and ephemeral trust models. Access is granted only after authenticating the identity and security posture of each access request. To eliminate unauthorized access to data and services and ensure secure access, the focus is on strong authentication, authorization, and granular access controls. Zero Trust Architecture includes several components.
What is Zero Trust architecture and its components?
Zero trust access
Access requests to resources are first made to the control plane, where the device and user must be first authenticated then authorized to gain access. When access is granted, the data plane will be signaled to accept traffic from the client.
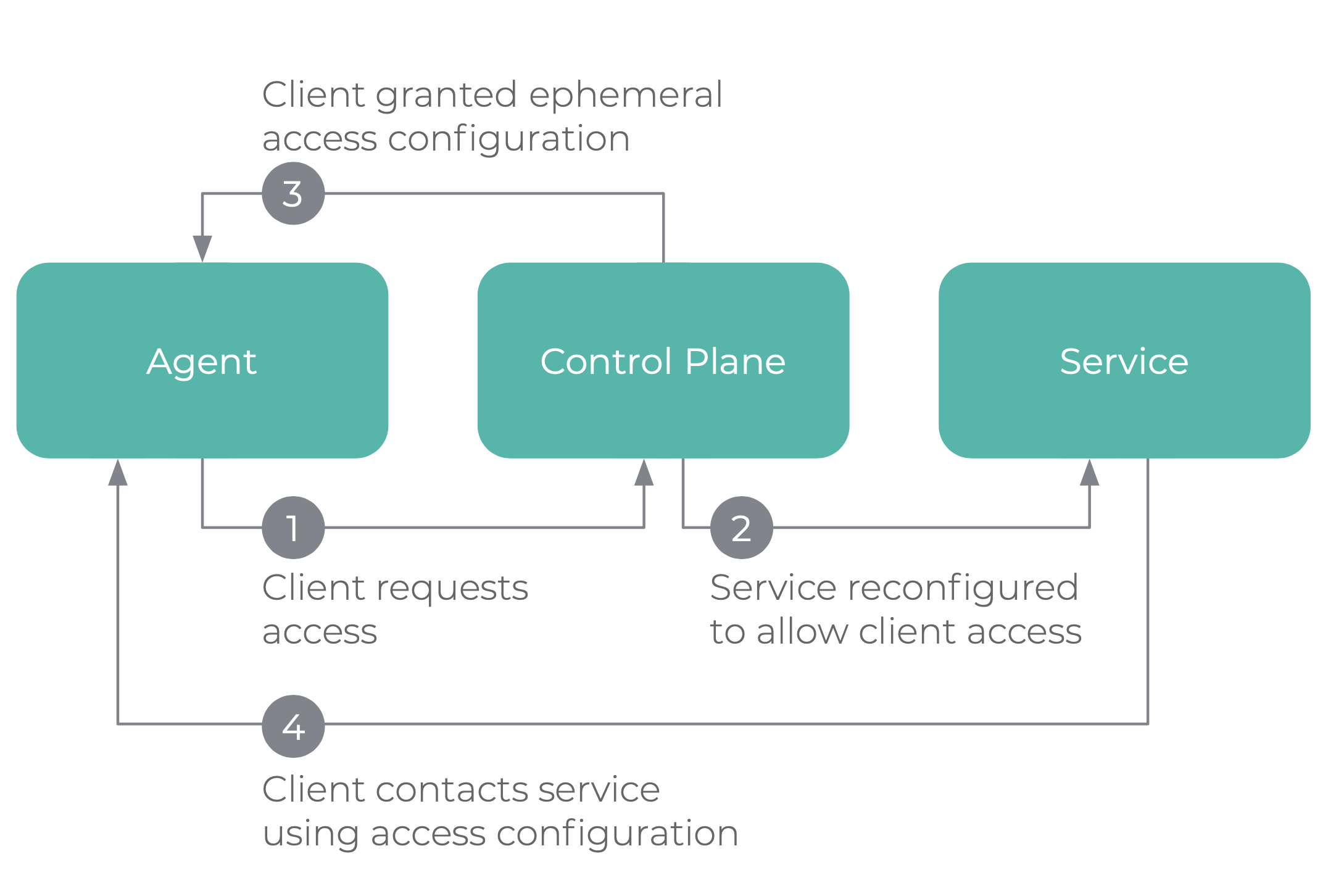
The network agent
In order to grant access, the system must know key information, such as the user, device and requested application access - enriched with its attributes. This is known as the “network agent”. This information must be updated continuously, in real-time due to the always-evolving nature of the threat landscape. With Fyde’s Zero Trust implementation, you can check roles and groups for user authorization, device’s OS version, the status of disk encryption, firewall, passcode, and other attributes prior to granting access to resources.
Authorization and policies
Policies are one of the key elements of a Zero Trust architecture and are conceptually composed of the enforcement plane, the policy agent, the trust engine and datastores from which you get the attributes and can grant access or not. With Fyde, you can enforce several policies to ensure secure access and gain more control:
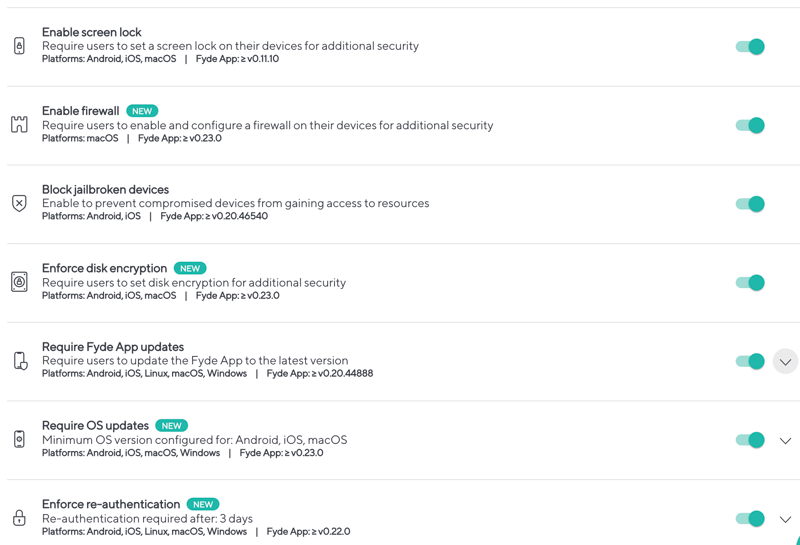
Devices
In order to trust devices, they must comply with a set of requirements. Each device has a unique certificate, signed by a private Certificate Authority and the private key is protected using the hardware security module, if available.
Users
Device trust and user trust are not the same; each must be independently authenticated. Fyde integrates with your Identity Provider for user authentication and allows you to implement granular authorization based on RBAC and ABAC.
Traffic
The network is always assumed to be compromised, so you must ensure confidentiality. Encryption must be deployed regardless of the “network zone”. Confidentiality must be ensured to protect the company data and those accessing it.
What is a ‘must’ in Zero Trust?
In a Zero Trust architecture, all network connections must be authenticated and should be encrypted. Authentication and encryption are performed by the Fyde agent at the endpoint, based on Fyde’s private PKI infrastructure. Device attributes are checked on the fly for each new connection.
Fyde Zero Trust architecture
The Fyde architecture relies on three main components: an app on the device (Fyde App), a proxy on each protected network (Fyde Access Proxy), and an administration console (Fyde Enterprise Console). The Fyde app operates at the network layer. When a device starts a connection to a protected resource, the Fyde App intercepts it and opens a mTLS connection with the Fyde Access Proxy, sending the device and user attributes to Fyde Enterprise Console which evaluates the policy. The Fyde Enterprise Console will check the attributes and allow or deny the connection to the resource, based on admin-configured policies.
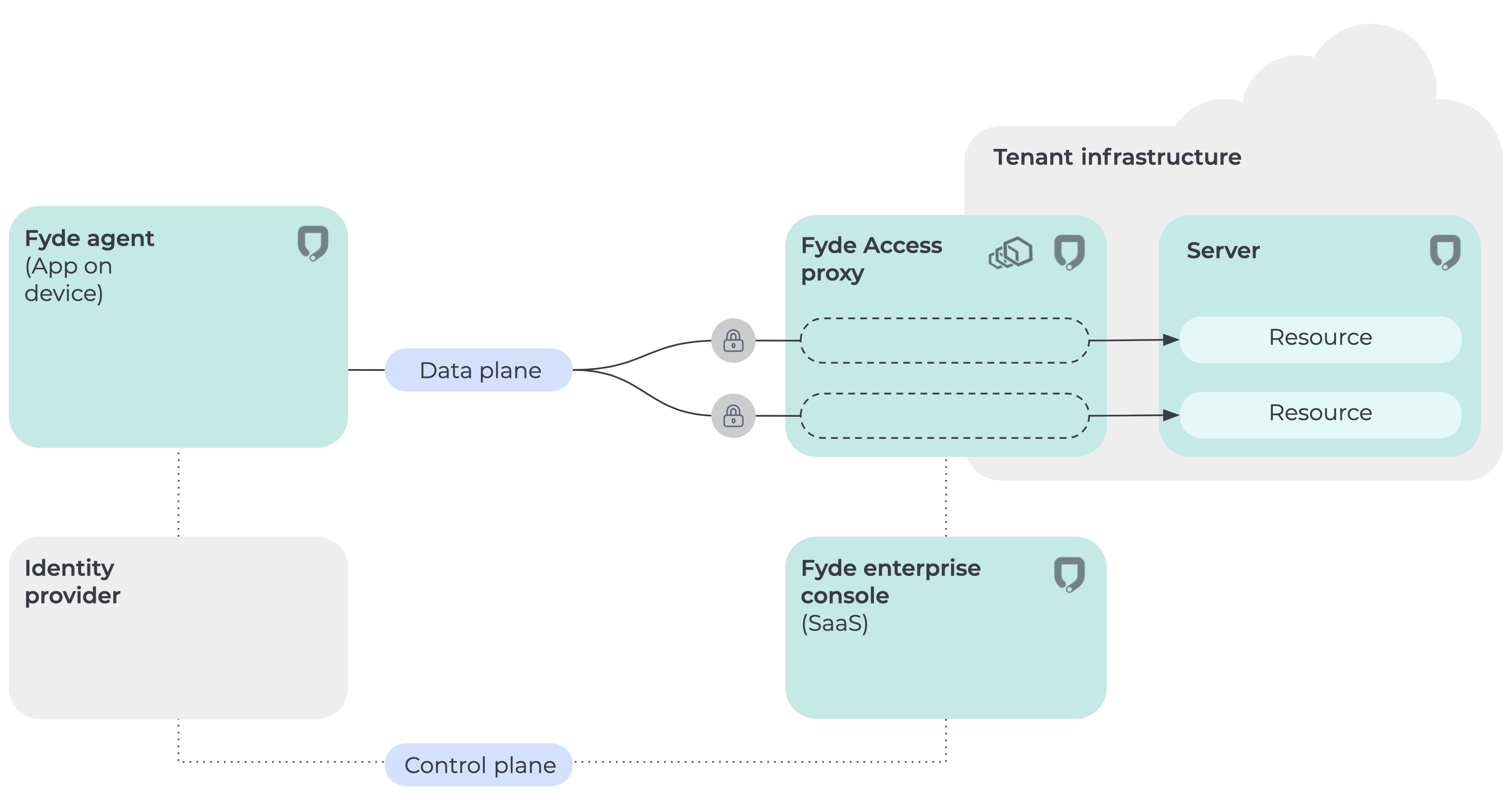
Zero Trust architecture is the modern way to ensure secure access in the enterprise. Fyde simplifies the path to Zero Trust for IT and end-users and improves control and visibility into secure access.
Learn more about Zero Trust:
Remote workers need a security upgrade. How Zero Trust can help
What is Zero Trust and how can it transform your enterprise security?
Startups need to prioritize security. Zero trust can be a lifesaver