-
Tags
-
Author
-
Sinan Eren
-
July 13, 2018
Remember the good old days, when you thought 2FA (two-factor authentication) could save your company and your customers from insidious phishing attacks? Well it is a new day, and phishers have once again proven that they can circumvent what we thought were robust security controls. The latest victim? 2FA.
How do they do it?
Many companies, especially in the financial services industry, have implemented 2FA. Vendors like Duo, Okta, RSA and others have generated millions from this technology. To date, it has been very effective in protecting consumers and employees from phishing and other credential theft attacks. However it is now becoming apparent that there was a rather lousy assumption by these companies in regards to their adversaries’ ability to orchestrate active attacks.
First, we have tracked attackers that were deploying active phishing attacks that manipulate their victims to enter their 2FA token as part of login process. This easily achieved by open-source web proxies like nginx that sit in the middle and relay every bit of information back and forth between the victim and the actual service. Typically this attack succeeds in obtaining a long-lived access token to the service and the entire account is compromised from there on.
Second, we tracked an even more elaborate MitM proxy setup by phishers which essentially downgrade two-factor authentication from other more robust methods such as hardware token to text message. Here is the illustration of this attack on Gmail:
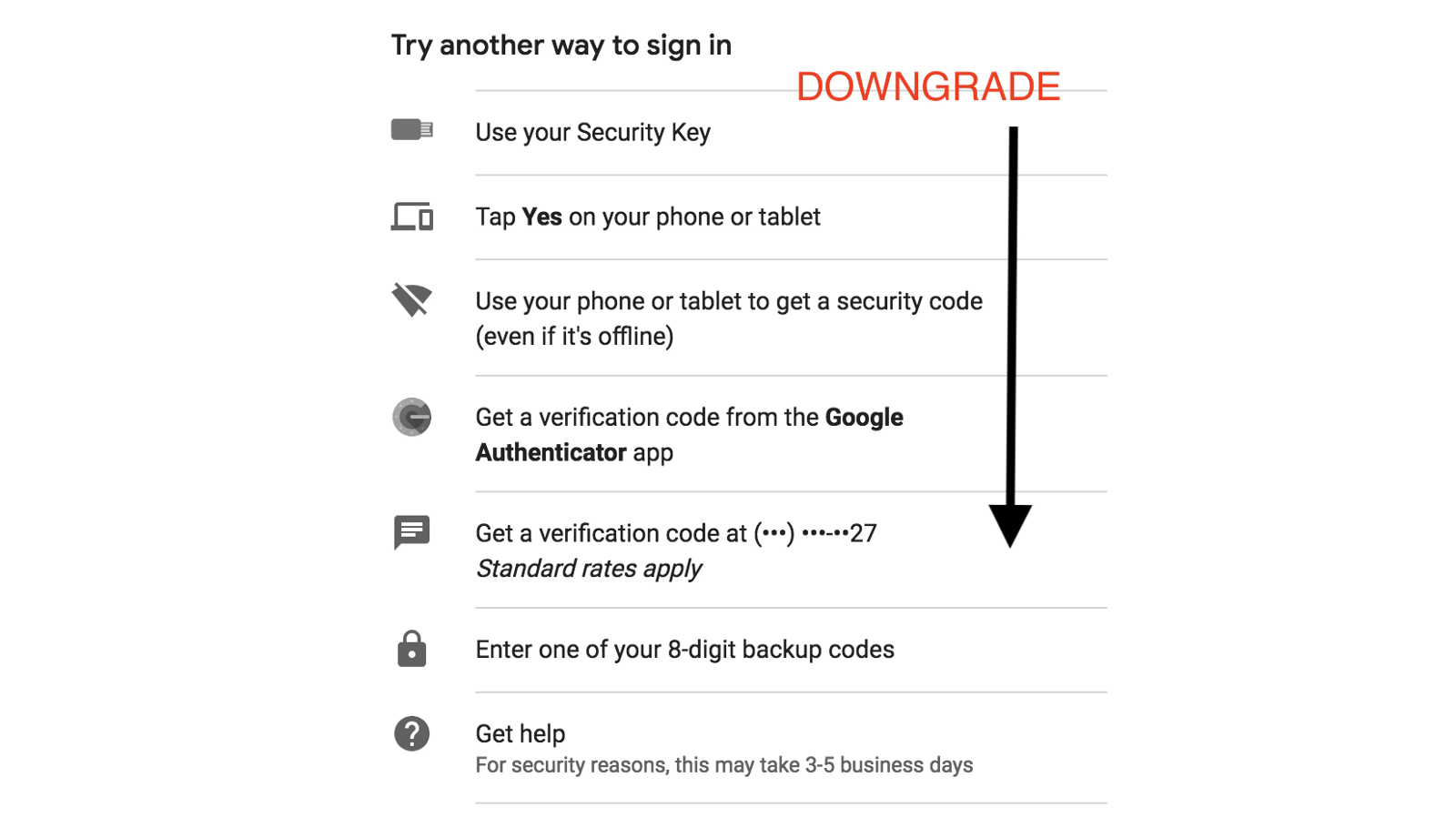
In this particular attack scenario, a user will receive an authentic-looking text message from a short-code purporting to be Google, telling the victim to sign in due to an urgent security or fraud related activity – the urgent “call-to-action” part of most phishing lures. When the user attempts to sign-in, the phishing proxy will relay the information to the original site, in this case accounts.google.com. Once the user enters their username and password, the man-in-the-middle phishing proxy will force the downgrade from the user’s favored method to text-message, effectively breaking hardware-assisted robust solutions, such as universal two-factor (U2F).
You might ask, why do Gmail or companies on Google Apps let 2FA method downgrades ? Answer is simple, cost of dealing with user support and lost/forgotten hardware tokens. We have yet to talk to a company that disabled all 2FA methods and left hardware token as the only factor.
What Can You Do?
What are the choices for an organization that has invested in 2FA? First, 2FA is still a much better solution than passwords alone and can be cost-effective for those with a limited budget.
In order to maintain the integrity of your solution, consider one of the following options:
1. Implement U2F and disable all fallback options.
This is a simple and fail-safe defense mechanism. Just be aware that this approach may increase your customer and IT support / call center load. Users will be required to contact you directly rather than relying on automated options. This might not be practical for some organizations, especially consumer businesses.
2. Deploy an active anti-phishing solution.
In addition to 2FA, that can detect and block this attack vector. These solutions will help you gain more visibility to suspicious links send to your users and extract additional value out of your threat intelligence datasets.
As everyone in the industry knows, the job of a security practitioner is never done. Each new defensive technology is viewed as a new challenge to the equally diligent practitioners on the offensive side. Our best advice? No security technology is a magic bullet, no matter what the vendor may tell you. Stay on top of attack trends and constantly reinvent your security program.