-
Tags
-
Author
-
Evelina Sinkevičiūtė
-
July 27, 2019
Imagine the following scenario. You just woke up on a Monday morning and started getting ready for work. You meditated, did a few pushups, and just as you took your first sip of coffee, 'ping' - you got a notification.
It's your boss. You open the email, and there's a request for a favor. Your boss asks you to buy 11 iTunes gift cards which she will give to team members as a nice appreciation bonus.
There’s a twist, she needs them in less than an hour. You think it's an excellent idea to reward employees and clarify the amount needed and the value. She’s being pretty generous and suggests $100 per card. You offer to bring the cards to the office, but your boss says she's off to a meeting and prefers that you email the gift card information. Additionally, she asks you to scratch the backs to reveal the codes and then send pictures of the gift card codes. To be more clear she shares an example picture, and you download it. This seems a little odd, but she’s the boss, so you don’t question it.
You leave your coffee and head out to buy the cards. Fifteen minutes later you hold 11 iTunes gift cards in hand, take pictures of the codes and send them to your boss.
Here's what just happened. She wasn't your boss, and you got scammed. Sadly, you're not getting that iTunes gift card. At least not this time.
We didn’t make this story up. It is a well-known scam, and one of Fyde’s employees, James, received this email recently. Instead of deleting it, he decided to scam the scammers.
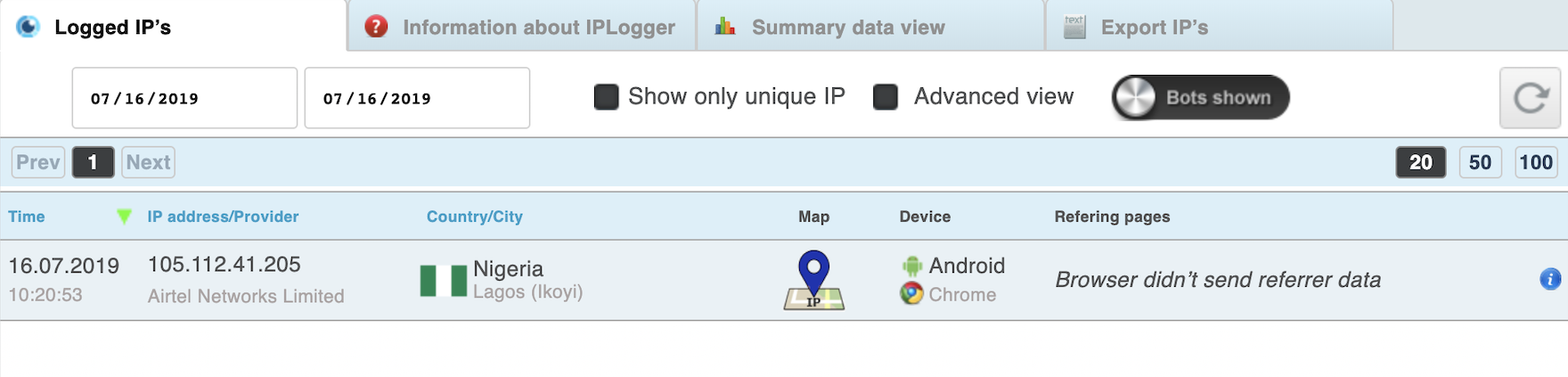
James created a trackable link, which directed to the 5 Ways to Spot a Phishing Email page, and sent it to the unaware scammer. A few minutes later, the scammer opened the link in Lagos, Nigeria on an Android phone.
The scammer: “Nice try.”
James: “How’s the weather in Lagos?”
The scammer: “Are you from Lagos?”
James: “I am not but you are.”
The scammer: “Which street am I in Lagos?”
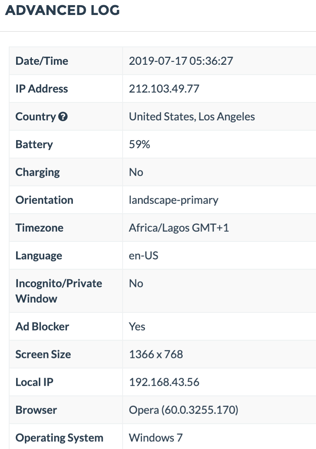
James added the scammer’s location, device information and (funny enough) added a new trackable link Don't Click On Strange Links: 6 Tips To Avoid Phishing Attacks. The scammer clicked on the link again, but this time on a Windows 7 desktop, with an Opera browser, and an IP in Los Angeles, California. The scammer wanted to hide his location by using a VPN, but when we checked the logs, the device's timezone was still 'Africa/Lagos GMT+1".
What to look for in a phishing scam
Always check the sender's email address
When you receive an email with a query to share any personal information, click on the links, or purchase anything, first, verify the sender's email address. If the sender is a colleague, double-check their email address. If the sender is from a service you use - email them separately or give a quick call. In our case, James recognized the fake email address of Fyde’s CEO.
Beware of urgent requests
If someone urges you to make a quick decision or share information urgently - don’t rush. Attackers like to play on your emotions because you’re more likely to think less and listen to instructions more. If the urgent request is from someone you know, follow up with them by giving a quick call or message via another platform.
Don’t download attachments or click on links
By downloading that innocent gift card code image, you could install some malicious software and put not only your personal information but also your company’s at risk. Before downloading any files, ensure you can trust the sender.
What is phishing?
Phishing is a form of fraud that uses both social engineering and deception. It aims to steal personal identity data, financial account credentials, or any other valuable data.
Although phishing emails and messages appear to be from a reliable source, they usually contain malicious links or attachments. Victims are prone to click on these malicious links or download attachments because they trust the source. The consequences can range from installing a fraudulent software to having login credentials or account information stolen.
To execute a successful phishing attack, an attacker may use link manipulation techniques or URL hiding. By creating a malicious URL, which at first glance appears to be legitimate, attackers trick victims into clicking on the link and getting the bait on a hook.
Another phishing tactic is link shortening, using services such as Bitly and others to hide the link destination. To register malicious domains, attackers use different alphabet or numeric characters, which when read quickly appear to look like the legitimate domain name. This technique is called homograph spoofing, where numbers 0 or 1 can be replaced by the letters O and I and can appear as, for example, mïcrosoft.com.
What is spear phishing?
Spear phishing is a trickier version of phishing which contains personal and convincing information to trick victims into doing things the attacker wants them to do. Usually, attackers research and collect victim's personal information on social media sites and style the emails to mimic the legitimate brands or people you know.
Learn more about phishing and its forms.