-
Tags
-
Author
-
Luísa Lima, Co-Founder & VP Engineering
-
February 6, 2020
How Fyde implements Zero Trust
Zero Trust architecture is the modern way to ensure secure access to the enterprise. Fyde simplifies the path to Zero Trust for IT by improving control and visibility into secure access, and for the end-users, by providing security, simplicity, and productivity.
Fyde focuses on protecting sensitive data and systems by enforcing policies that rely on user and device attributes at the endpoint level.
Fyde Zero Trust architecture
The Fyde architecture relies on three main components:
-
Fyde App;
-
Fyde Access Proxy;
-
Fyde Enterprise Console.
Fyde system architecture:
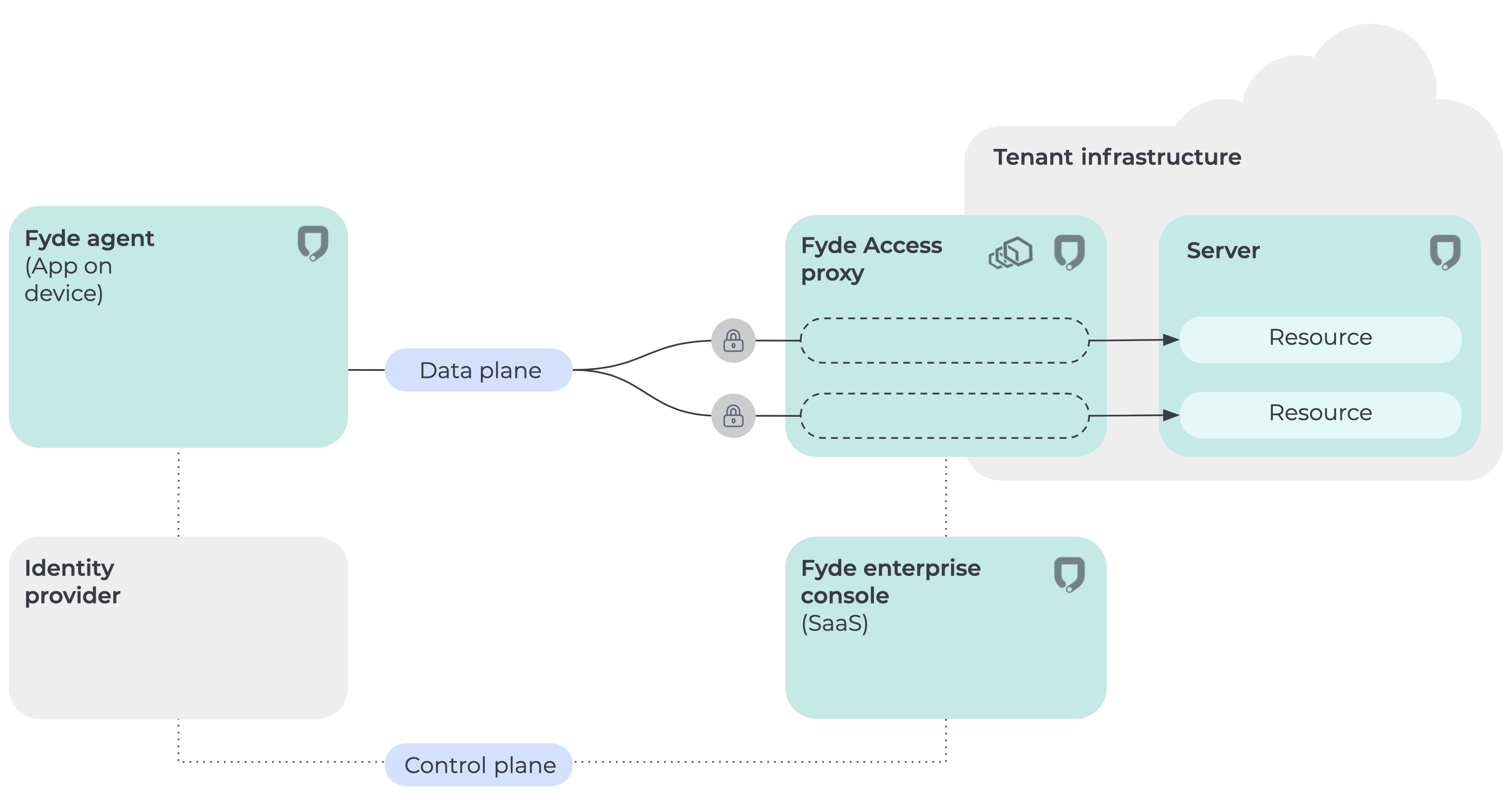
Fyde was built to solve current VPN problems and enable modern enterprises to thrive, powered by the Zero Trust concept. Now, let’s dig deeper into how Fyde implements Zero Trust.
Network protection
The Fyde app operates at the network layer. When a device starts a connection to a protected resource, the Fyde App intercepts it and opens an mTLS connection with the Fyde Access Proxy, sending the device and user attributes to Fyde Enterprise Console which evaluates the policy. The Fyde Enterprise Console will check the attributes and allow or deny the connection to the resource, based on admin-configured policies. Read more about Zero Trust architecture and components.
Fyde’s implementation abstracts from the network itself. All that we consider is a device (with an authenticated/identified user) and an end resource. In fact, unlike a VPN, you are not connecting to an end network, but rather to an end resource, via the Fyde Proxy. If you use a traditional VPN, the protection relies on the perimeter. Imagine that you have a protected application called VeryImportantApp that is available on the corporate network. To connect to the application, you first turn on your VPN, which routes your traffic to the corporate network; then, you connect to VeryImportantApp.
Fyde works very differently. Instead of using a VPN, VeryImportantApp is accessible via Fyde.
-
First, VeryImportantApp is set up behind the Fyde Proxy. Then, when you connect to VeryImportantApp, Fyde app detects that it is a protected resource and intercepts all traffic to VeryImportantApp.
-
Fyde sets up a mutually authenticated tunnel to the Fyde Proxy that serves VeryImportantApp. This means that the Fyde app authenticates the proxy and the proxy authenticates the Fyde app.
-
All traffic then flows encrypted from the Fyde App to the Fyde Proxy, and then finally, to VeryImportantApp.
What happens if you are inside the corporate network? The answer is - the same. VeryImportantApp is no longer accessible without the proxy. In fact, if you turn off your Fyde app, your operating system will no longer be able to route to VeryImportantApp.
Resource mapping
When a device enrolls in a tenant using Fyde, after the certification process, it receives a list of hashed protected resources from the Fyde API. This way, when a user wants to connect to a resource, the Fyde app knows that it should intercept communications to the resource; it will then request a resource access token from the API, which includes the proxy to connect to.
Identities and devices
When you enroll a user on the Fyde console, Fyde generates an enrollment URL that includes a token that is valid only for enrollment. This URL can be sent via email or via any provisioning mechanism that the sysadmin decides to use. When a device is enrolled using this enrollment URL, first, we request the user identity and confirm it using the tenant Identity Provider; then, we generate a certificate that is unique to the device, which is stored in the device hardware secure enclave. This way, there is a strong identity connection between the device and the user, which is not present in other systems.
When the Fyde app starts a connection to a protected resource, then, the certificate device is used to authenticate it; furthermore, the device attributes are collected by the Fyde App, forming a JWT token which is sent to the Enterprise Console for policy validation. The Enterprise Console also uses the same device certificate to form a JWT token which is shared with the Fyde Proxy, if access is granted.
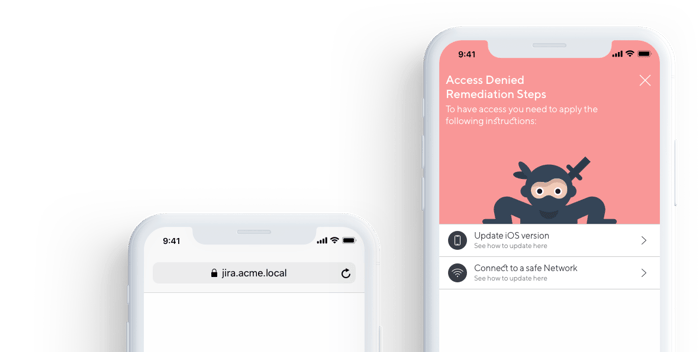
Remediation engine
When a connection to a resource is denied, the Fyde app receives a list of attributes that are not compliant with the policy/policies configured for the resource, together with a list of steps that the user can perform to fix the issue.
For example, imagine that with one of the access policies you require users to enable a firewall on their devices. If a user doesn’t have a firewall enabled/turned on - Fyde will deny access to resource VeryImportantResource. Then, the app will receive a response from the API that includes the reason for the denied access and the step how to fix it: “enable firewall”, together with a URL that links to specific content that shows the user how to turn it on.
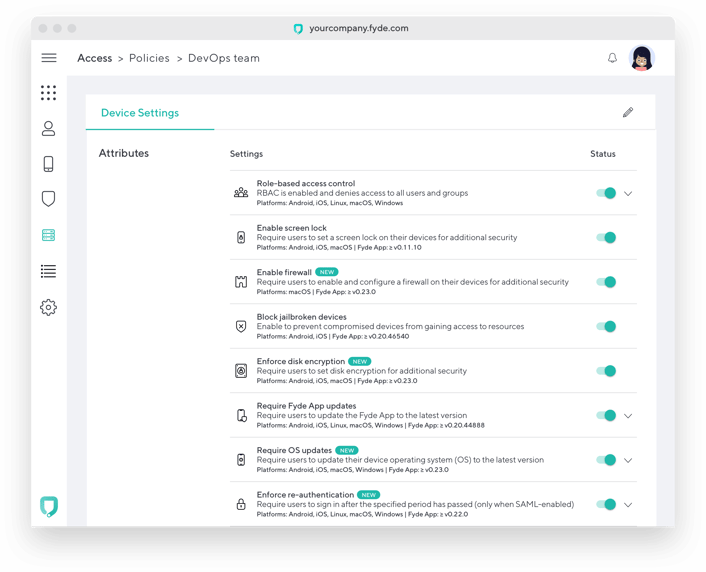
Access policies
Access policy configuration is a very simple API that sets a list of supported policies for a resource in Fyde. One of the most interesting parts of the Fyde setup is that the Fyde app runs at the device level, and as such, can collect attribute details in order to enforce policies.
Fyde deployment time
Setting up Fyde up is very simple. You deploy a proxy in front of resources you want to protect (as a rule of thumb, we deploy one proxy per network, but that depends on the configuration), and configure the resources on the Fyde Enterprise console.
To enroll the users and devices, Fyde has a certification-based mechanism that is completely seamless for the admin and only requires an email. MDM is not required. To set up most other solutions, you need complex VPN and network segmentation configurations.
Fyde and other technologies
Behind the scenes, we use Hashicorp Vault to handle certificate management and ElasticSearch for our data stream. But more important than the technologies we use is what we do with them. We developed an open-source Fyde cli in Go that wraps the Fyde API, has all the functionality of the Fyde Enterprise console and can be used for infrastructure as code setups, which allows you to automate not only your networking and deploys, but also your security!
Fyde vs other solutions
Fyde’s approach to Zero Trust distinguishes Fyde Enterprise from other VPN and Zero Trust solutions:
-
Fyde does not expose the enterprise network by allowing access to only the required resource, it monitors user identities, devices’ security status.
-
Fyde supports BYOD by validating device security to access your infrastructure.
-
Fyde ensures retrospective and prospective device security and detects if the device was exposed to an attack before.
-
Fyde ensures role and attribute-based access control to ensure access for traveling employees and partners.
-
Fyde enables continuous connectivity with a built-in defense and local proxy on a device.
-
Fyde, unlike any other VPN solution in the market, protects and blocks threats on your device.
-
Fyde’s built-in remediation engine lets users fix access issues themselves and increases awareness of the device security.
Read more about the differences between Fyde vs VPN.
Alternatively, check out Zero Trust security: the ultimate guide to learn more.